This post is based on Horizon on VMware Cloud on AWS deployment. In this post I’m assuming UAG and Connection Servers (CS) are hosted on VMware Cloud on AWS SDDC and utilizing native AWS Elastic Load Balancer (ELB) to load-balance UAG and CS sessions.
User Access Scenario: External user hits AWS internet facing ELB (2) via AWS IGW and access request get redirected to UAG hosted on VMC SDDC (3). UAG forwards the request to internal ELB (4) fronting CSs hosted on VMC SDDC and internal ELB forwards the request to one of the CS(5). Finally, CS authenticates the user and allocates desktop(6).
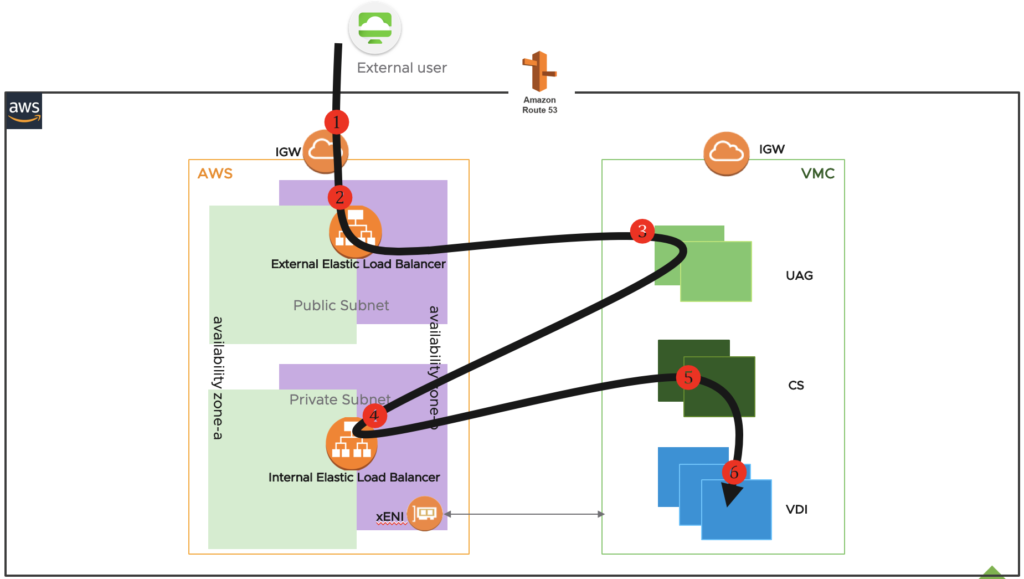
Note: In above scenario, horizon protocol traffic routes via AWS gateway. However, desktops internet traffic route to public internet via VMware cloud on AWS SDDC internet gateway.
Please follow the Doc VMware document for UAG deployment and follow my other post for AWS Elastic Load Balancer (ELB) deployment and configuration. After you deployed UAG and ELB, follow below steps.
- Log in to UAG admin console (admin/password) and select Configure Manually.
2. In General Settings section, select show Edge service settings>click in gear icon right to the horizon settings and configure as below and Save the configuration.
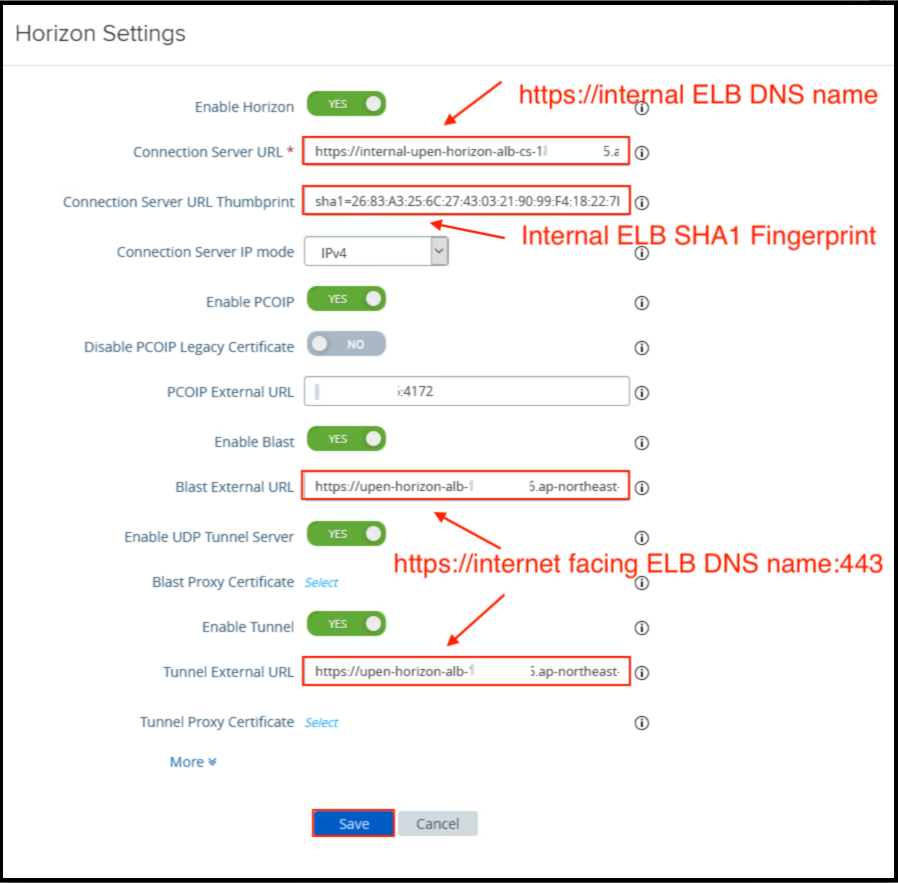
In my test environment I’m using internet facing ELB DNS name for Blast and Tunnel External URL. For production, you can use AWS Route 53 service and create domain CNAME record against external ELB DNS name. i.e.; vdi.yourcompany.com.
3. After you saved the configuration, status of Horizon Settings under Edge Service settings becomes Green like below.
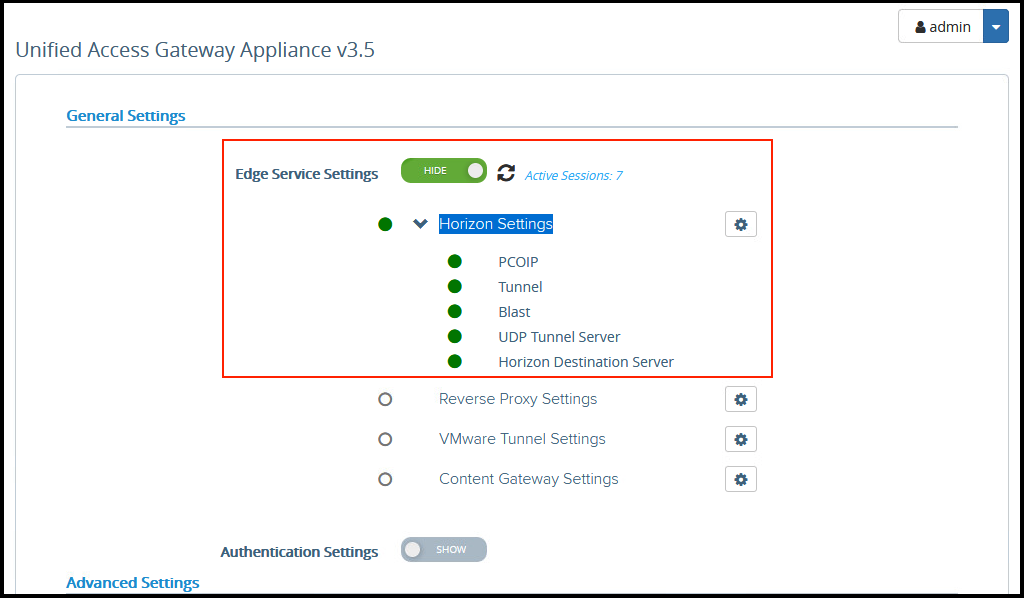
4. There are 2 UAG behind the internet facing ELB. You should follow the same steps as above for all UAGs exist in environment.
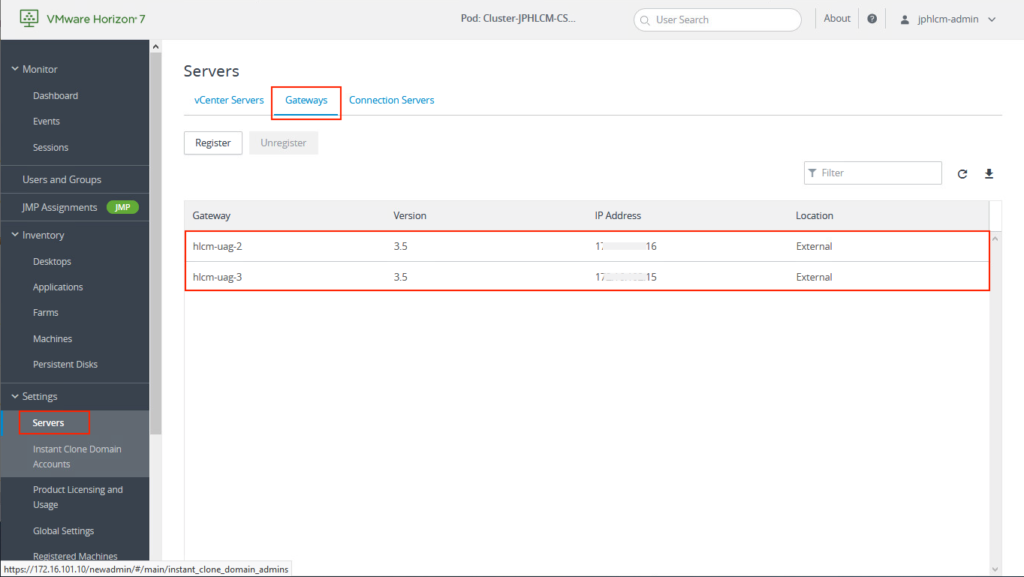
Load Balancing test
Test Scenario: 2 users are logging into horizon desktops from public internet. Sessions are allocated to different UAG and Connection servers.
UAG sessions: Users’ sessions are in 2 different UAGs.
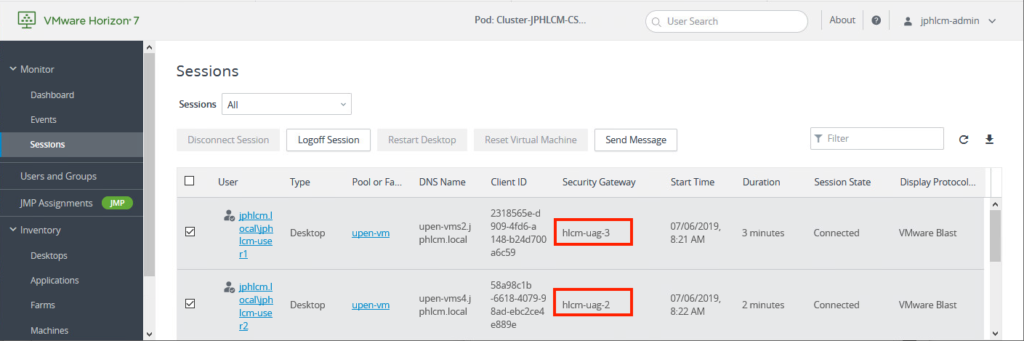
Connection Server Sessions: Users’ sessions are in 2 different connection servers.
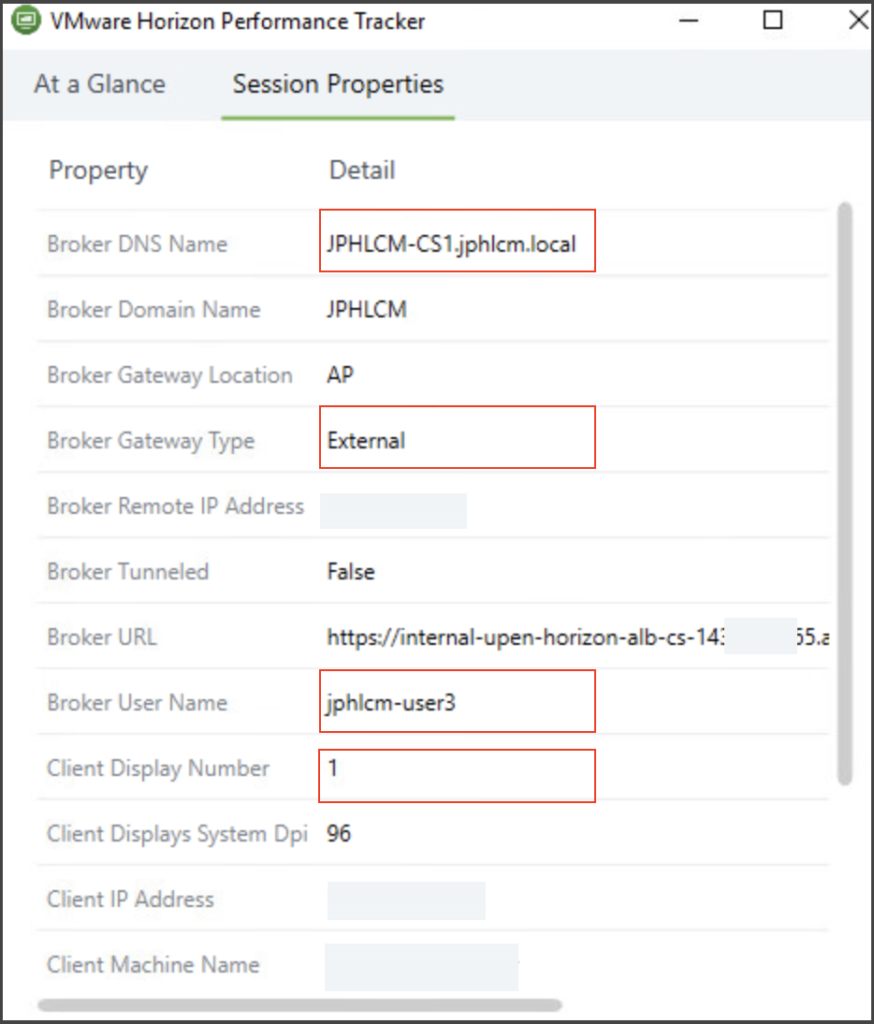
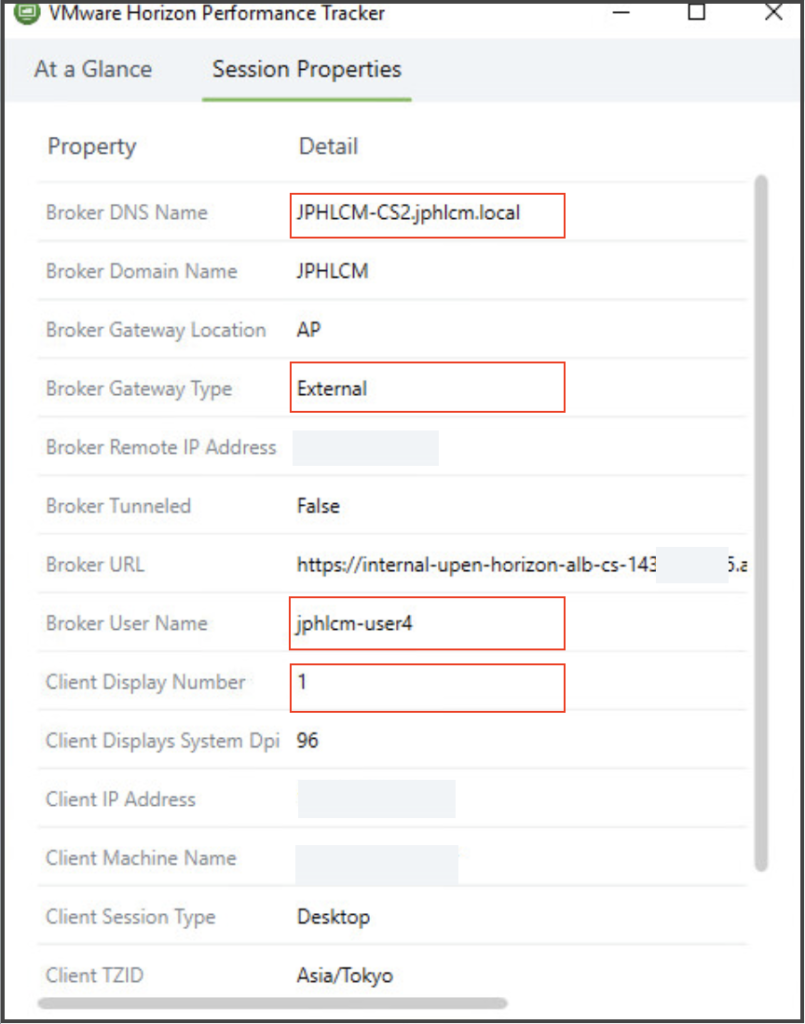
![]()